Structure of Hair and its Characteristics
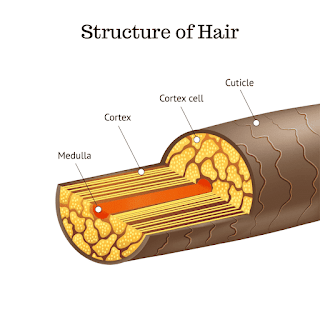
Structure of Hair 1. Cuticle The cuticle is the outermost translucent layer of the shaft of the human hair. It is smooth and flat and acts as a protective layer for the hair. The cuticle looks like fish scales or roof tiles. It is an important part of the hair that determines the hair species. 2. Cortex The cortex is the middle layer of the hair which is made up of long thin cells. It consists of long keratin filaments that are held together by disulfide and hydrogen bonds. It also contains the natural hair coloring material (pigment) which is called melanin. It provides stability, elasticity, and a unique color to the hair. 3. Medulla The medulla is the central core of the hair which is composed of soft keratin protein which may be either absent or present. If present, it may be fragmental, interrupted, or continuous. It is absent in some species and does not determine the species of hair. Characteristics of hair to determine the species, race, sex, and site 1. Color The color o...